From 78ae8153a03944f7ac99521f67bd2f0de7887f4d Mon Sep 17 00:00:00 2001
From: David Geddes <38050281+david-maidsafe@users.noreply.github.com>
Date: Tue, 16 Oct 2018 10:23:03 +0100
Subject: [PATCH 1/2] chore/readme: update ReadMe.md (Crust updates)
Revise readme.md file to take account of changes to Crust
---
README.md | 30 +++++++++++++++++-------------
1 file changed, 17 insertions(+), 13 deletions(-)
diff --git a/README.md b/README.md
index 297896dd1..193ec2701 100644
--- a/README.md
+++ b/README.md
@@ -9,29 +9,33 @@ Reliable p2p network connections in Rust with NAT traversal. One of the most nee
| [MaidSafe website](https://maidsafe.net) | [SAFE Dev Forum](https://forum.safedev.org) | [SAFE Network Forum](https://safenetforum.org) |
|:----------------------------------------:|:-------------------------------------------:|:----------------------------------------------:|
+
## Overview
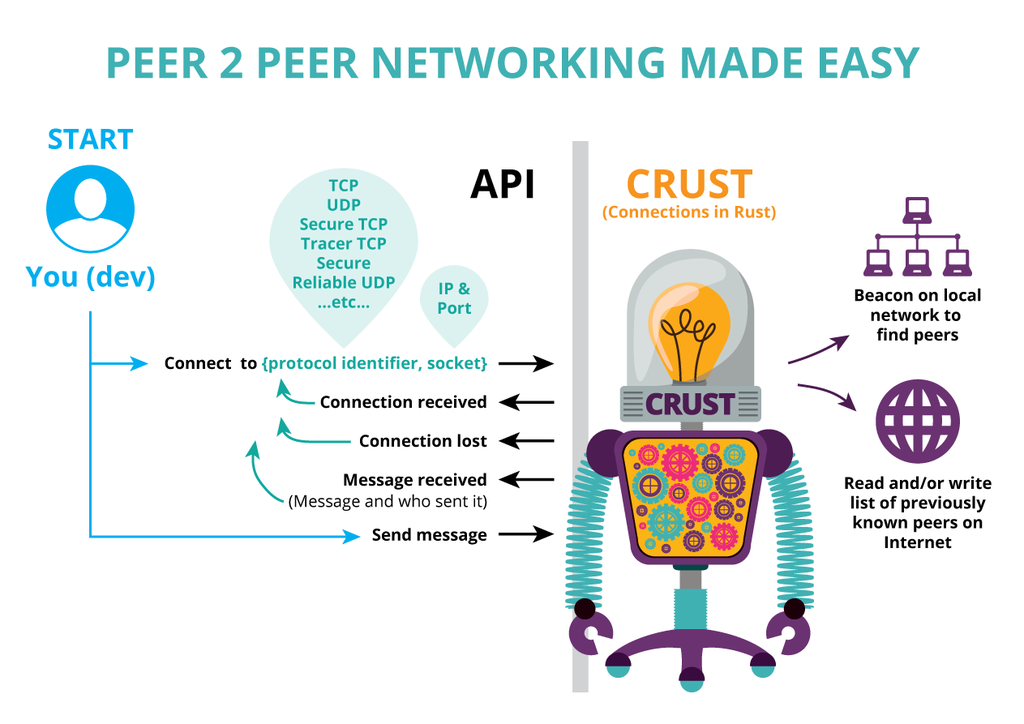
-This library will allow p2p networks to establish and maintain a number of connections in a group when informed by users of the library. As connections are made they are passed up and the user can select which connections to maintain or drop. The library has a bootstrap handler which will attempt to reconnect to any previous "**direct connected**" nodes.
+Crust is a low level networking library that is optimised for peer-to-peer connections and data transportation. It implements primitives to connect two peers together and start exchanging messages in a secure, reliable way. It supports **multiple protocols** ([UDP](https://en.wikipedia.org/wiki/User_Datagram_Protocol) and [TCP](https://en.wikipedia.org/wiki/Transmission_Control_Protocol) hole-punching) and it is crypto secure - all communications, starting with handshake messages, are encrypted. It also provides other security features like randomised ports that are used to prevent targeting a particular known port to conduct DoS attacks. Crust implements several [NAT traversal](https://en.wikipedia.org/wiki/NAT_traversal) techniques such as hole punching and use of [IGD](https://en.wikipedia.org/wiki/Internet_Gateway_Device_Protocol).
-TCP connections are always favoured as these will be by default direct connected (until TCP hole punching can be tested). TCP is also a known reliable protocol. Reliable UDP is the fallback protocol and very effective.
-The library contains a beacon system for finding nodes on a local network, this will be extended using a gossip type protocol for multi hop discovery.
+
+## Upcoming Features / Benefits
-Encryption of all streams will also allow for better masking of such networks and add to security, this is done also considering the possibility of attack where adversaries can send data continually we must decrypt prior to handling (meaning we do the work). There are several methods to mitigate this, including alerting upper layers of such activity. The user of the library has the option to provide a blacklisting capability per session to disconnect such nodes 'en masse'.
+
+### Multi-protocol expansion
+Adding to the existing TCP & UDP hole-punching protocols Crust will soon include TCP-direct and introduce µTP, which wraps UDP and adds reliability, congestion control and ordered delivery to make a more robust and a better paradigm. Supporting multiple protocols means that if a firewall/router does not support one particular protocol then the network switches to another to get connected. If the firewall/router supports all protocols then Crust chooses the 1st protocol that successfully establishes the connection.
-_direct connected_ == Nodes we were previously connected to. TCP nodes or reliable UDP nodes that allow incoming connections (i.e. direct or full cone nat that has been hole punched). This library also supports fallback endpoints being passed at construction that will allow a fallback should nodes from previous sessions become unavailable.
+
+### Secure serialisation
+The network encrypts everything handed to it for transportation automatically. With Secure serialisation we have negated MITM attack as everything on the network is encrypted at each network hop. Also, the node signing each packet provides non-repudiation as the sender cannot deny that they signed the packet.
-## NAT Traversal/Handling
-
-Several methods are used for NAT traversal such as UpNP and hole punching. [See here for TCP NAT traversal](http://www.goto.info.waseda.ac.jp/~wei/file/wei-apan-v10.pdf) and [here for UCP/DHT NAT traversal
- ](http://docs.maidsafe.net/Whitepapers/pdf/DHTbasedNATTraversal.pdf) etc. These methods will be added to by the community to allow a p2p network that cannot be easily blocked. By default this library spawns sockets randomly, enabling nodes to appear on several ports over time. This makes them very difficult to trace.
+
+### Bootstrap cache
+Bootstrap caching enhances the concept of using genesis nodes (hard-coded addresses) for initial vault detection by dynamically creating a list of nodes which are directly reachable without the need to hole-punch. This list is appended and pruned as nodes connect/disconnect to the network so is always kept up-to-date.
+
## License
+This Crust library is dual-licensed under the Modified BSD ( [LICENSE-BSD](https://opensource.org/licenses/BSD-3-Clause)) or the MIT license ( [LICENSE-MIT](http://opensource.org/licenses/MIT)) at your option.
-This SAFE Network library is dual-licensed under the Modified BSD ([LICENSE-BSD](LICENSE-BSD) https://opensource.org/licenses/BSD-3-Clause) or the MIT license ([LICENSE-MIT](LICENSE-MIT) http://opensource.org/licenses/MIT) at your option.
-
-## Contribution
-
+
+## Contribute
Copyrights in the SAFE Network are retained by their contributors. No copyright assignment is required to contribute to this project.
From 5e672b2e85c0a3c61576989e5b37c0f7b4c24eff Mon Sep 17 00:00:00 2001
From: Nikita Baksalyar
Date: Wed, 17 Oct 2018 16:51:57 +0100
Subject: [PATCH 2/2] chore/ci: disable clippy/rustfmt temporarily
---
.travis.yml | 26 ++++----------------------
1 file changed, 4 insertions(+), 22 deletions(-)
diff --git a/.travis.yml b/.travis.yml
index de32b6a10..266fbb9e2 100644
--- a/.travis.yml
+++ b/.travis.yml
@@ -2,17 +2,13 @@ env:
global:
- RUST_BACKTRACE=1
- PATH=$PATH:$HOME/.cargo/bin
- - RUST_STABLE=1.28.0
- - RUST_NIGHTLY=nightly-2018-07-07
- - RUST_RUSTFMT=0.99.2
- - RUST_CLIPPY=0.0.212
+ - RUST_STABLE=1.29.2
os:
- linux
- osx
language: rust
rust:
- - 1.28.0
- - nightly-2018-07-07
+ - 1.29.2
sudo: false
branches:
only:
@@ -22,22 +18,8 @@ cache:
before_script:
- curl -sSL https://github.com/maidsafe/QA/raw/master/travis/cargo_install.sh > cargo_install.sh
- bash cargo_install.sh cargo-prune;
- - if [ "$TRAVIS_RUST_VERSION" = "$RUST_NIGHTLY" ] && [ "$TRAVIS_OS_NAME" = linux ]; then
- bash cargo_install.sh rustfmt-nightly "$RUST_RUSTFMT";
- bash cargo_install.sh clippy "$RUST_CLIPPY";
- fi
script:
- - if [ "${TRAVIS_RUST_VERSION}" = "$RUST_STABLE" ]; then
- (
- set -x;
- cargo test --release --verbose
- );
- elif [ "${TRAVIS_OS_NAME}" = linux ]; then
- (
- set -x;
- cargo fmt -- --check &&
- cargo clippy && cargo clippy --profile=test
- );
- fi
+ - set -x;
+ cargo test --release --verbose
before_cache:
- cargo prune