-
Notifications
You must be signed in to change notification settings - Fork 104
Phishing For Remote LogOn Credentials
This Module allows attackers to Lock Target WorkStation and request for a valid UserAccount password to UnLock it. While in background it stores the credentials captured to a logfile (remote) under $env:tmp folder for later review, only then it will UnLock target WorkStation ..[url] enigma0x3 - phishing for credentials
Remark
-
NewPhish.ps1It keeps checking valid credentials againt the DC unless theprocess its stoped
-
CredsPhish.ps1will run (loop) when exec in a machine that does not haveLogOn password set
- ALL the Modules Used in this article does not require the Client to be executed with Admin Privs
Article Quick Jump List
1º - Sellect meterpeter 'PostExploit' Module

2º - Sellect meterpeter 'CredPhi' Module

3º - Sellect meterpeter 'OldBox' OR NewBox Module

This Module allow attacker to Lock Target WorkStation and request for a valid UserAccount password to UnLock it, While in background it stores the credentials captured to a logfile (remote) under $env:tmp folder for later review, only then it will UnLock target WorkStation ..
Old Credentials MsgBox (windows <7) - PostExploit -> CredPhi -> OldBox
 New Credentials MsgBox (windows >7) - PostExploit -> CredPhi -> NewBox
New Credentials MsgBox (windows >7) - PostExploit -> CredPhi -> NewBox

-
Remark:
- The meterpeter (Server) remains
frozenWhile a valid credential its not enter remotely (???).
- The credentials enter will be validated (or not) against the
DomainControlerorLocalMachine.
-
CredsPhish.ps1 will run in infinite loop when executed in a machine that does not have
the logon password set by default. (its set to run 1000000000 times before exit execution).

-
NewPhish.ps1 It keeps checking credentials againts the DC unless the process its stoped
- The meterpeter (Server) remains
1º - Sellect meterpeter 'ReadLog' Module
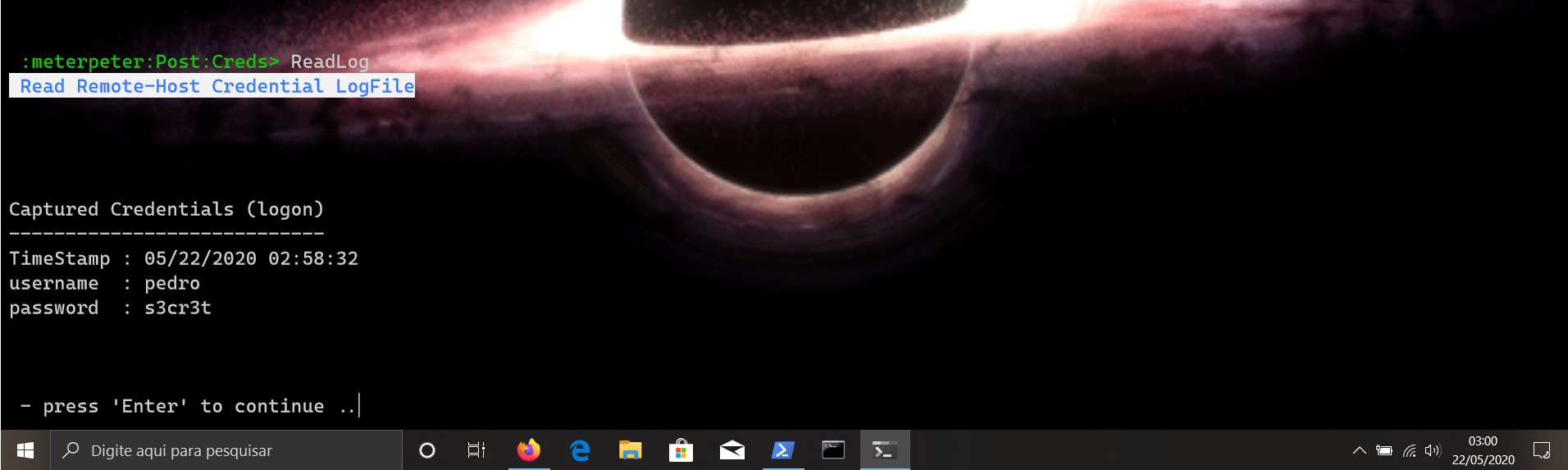
-
Remark:
- meterpeter will try to delete all
relatedScripts/Files left behind afterReadLogexecution.
- meterpeter will try to delete all